
How to avoid being frauded over email
Unfortunately there are many internet scammers out there. Some of them try to find their way to your private information through emails. This is called email spoofing. Learn how to spot the fraud and increase your security over email.
In the old-fashioned way paper letters are sent with an envelope on which you write sender and recipient - that way you know who the letter is from and where it should be sent to - for the most part. There is nothing that prevents you from writing someone else's name as sender with the aim of making the recipient think that you are someone else. It is in principle possible to cheat in this way also with physical letters, but it rarely has fatal consequences.
The case is different in the digital world where the fraud can be more easily camouflaged in many different ways which seem so real that we do not know we are being cheated until it is too late.
Just as you can change the sender with the letter you can also change the sender of emails in the digital world. This is an email instead of a letter, and the technique is called email spoofing. It is a technique so cunning that it is difficult to decode the danger signals.
The worst internet fraudsters will do anything to get hold of your private information even in your otherwise 'private' inbox. And this is despite the fact that all kinds of GDPR rules have been set up so you can control where your data ends up, and not least who ends up in your inbox.
And that is perhaps also why we already have great confidence that those who actually find their way to our inbox have good intentions and that they have ended up there for a reason because we ourselves have accepted it. In other words, we strongly believe that we know those who end up in our email inbox. But with email spoofing fraudsters have found a way to exploit precisely that trust.
What is Email Spoofing?
Email spoofing also called email forgery is an email where the sender pretends to be someone else with the aim of cheating confidential information out of the recipient.
It can for example be used to get the recipient to click on a link with malware, get the user to download malware via an attachment, get the recipient to send money, get the recipient to sign documents/procedures or otherwise phish confidential information about the person or the company. To understand it better here is an example:
Let us assume that you are employed at the company named "ExampleCompany". Suddenly you receive an email from someone in the company's "IT Department". In the email the sender writes that you must change your password to a system you use. And all you have to do is click on a link in the email and then enter your current login details.
You have already learned and heard countless times that you need to check if the senders are real. So of course you check that, and the sender's email is "Jens (it@ExamplelCompany.dk)" which looks valid. Therefore you may not see any warning signs and you decide to click on the link, and it looks very similar to the login system of the system you have been asked to change your password for. In good faith you follow the instructions and log in with your information and "change" your password and go on with your work day.
But what you do not know is that this email did not come from one in the it department but from someone pretending to be Jens and the link he sent you was a website that just looked like that system you usually use.
So the login information you entered on the fake website has now ended up in the wrong hands. The fake Jens can now log in as you in the real system. That is of course a big problem in itself but it is only worse if you like so many others do not use different passwords for different systems. If you use the same password for many system this "Jens" now also has login to these. And then there is serious danger afoot.
All this happened because you trusted for good reasons that it was a real colleague from the IT department who asked you to change your password. But unfortunately that was not the case. Instead it was email spoofing.
How Email Spoofing Can Look Like
The people who are really interested in cheating can relatively easily set up fake emails.
Unfortunately it is relatively easy to send an email that appears to come from a valid sender. Just like on a physical letter you can write a different sender than you on the "envelope" of an email.
Here is an example of what an email from a fake email could look like in your inbox.
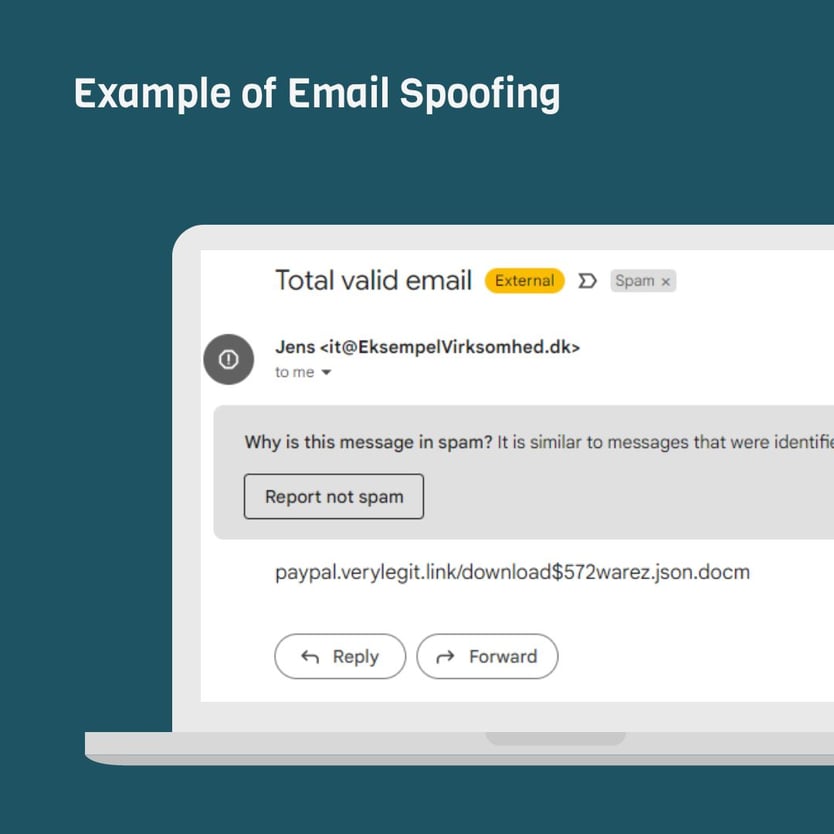
At first glance it really looks like an email from Jens in the IT department, and you can therefore quickly believe that the email is vaild and immediately have confidence in doing what the email asks for.
With the right settings you can also see in the image that it actually ends up in spam. But this does not mean that you are insured. In this case obstacles have been set so that the email ends up in the spam inbox but still not enough obstacles for it to end up in one of your inboxes at all.
How Can You Avoid Scam Emails?
Exactly the above example could have been avoided in many ways. You could check whether the address on the link is the same as the link in the right system. If the system supports multi-factor authentication it would be more difficult for fake Jens to cheat their way through. Fortunately, there are several ways to avoid being exposed to email spoofing.
The very best thing would of course be that you had never received this email or that it had ended up in your spam inbox. In any case it would be best if your email inbox could at least signal that the email was fake or otherwise dangerous. That would already give you the necessary red flags right from the start and maybe make you go past the IT department before you start doing anything the email asks you to do.
But you can actually make sure that your email inbox gives you warnings about suspicious and dangerous emails.
This can be done with a combination of the technologies SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) together with DMARC (Domain-based Message Authentication, Reporting and Conformance).
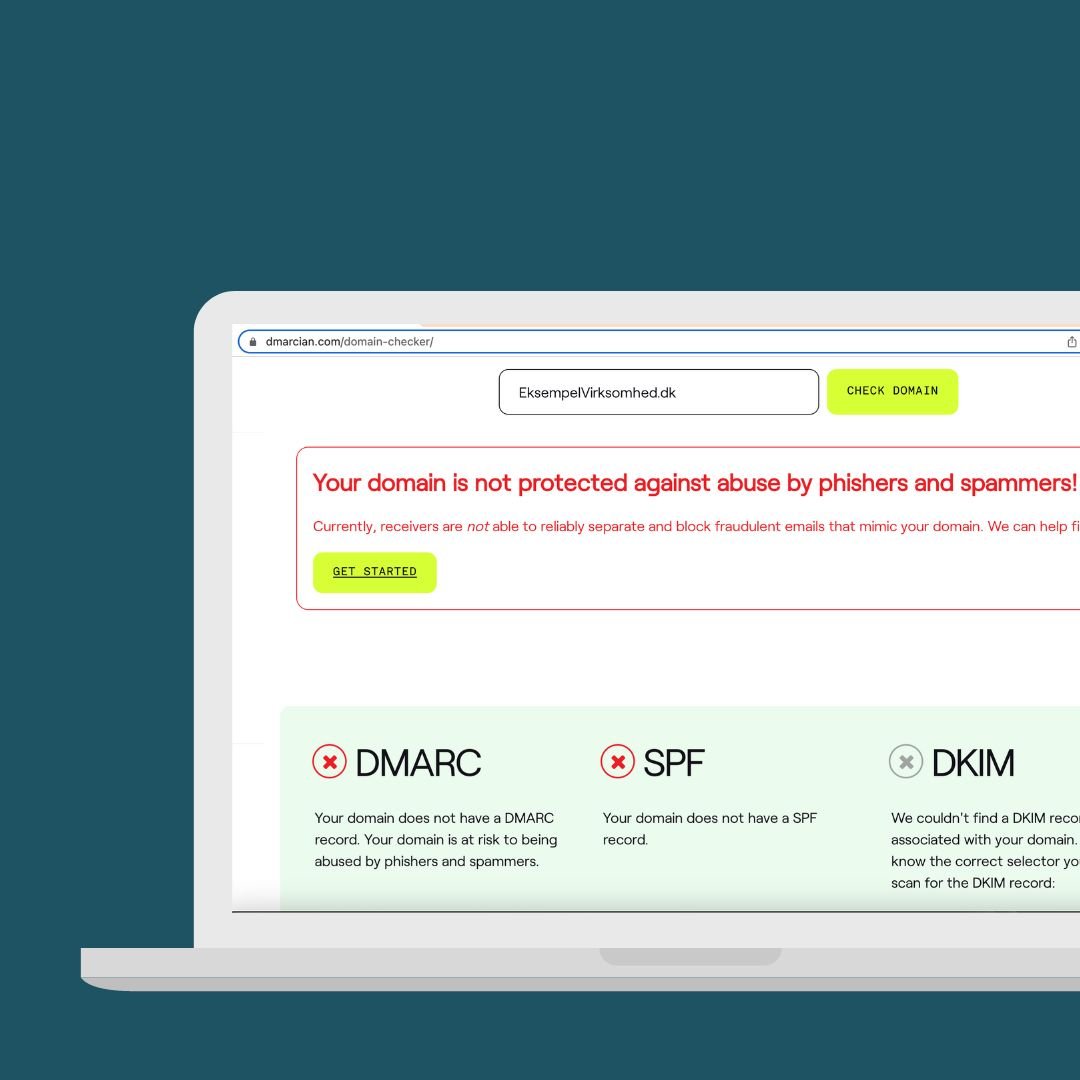
If you are in doubt whether it is already set up for your domain and whether you already have the necessary protection then you can check it here.
Below you can see that our example from earlier with 'ExampleCompany.dk' is in no way protected by these technologies:
What is SPF (Sender Policy Framework)?
SPFs purpose is to verify whether an email is valid or spam. It works by the recipient's mail server checking whether the domain the sender claims to be sending from contains an SPF record in one's domain setup (DNS).
SPF contains information about which servers may send email from your domain. Since fake Jens does not have control over your email server or your email provider's server he cannot easily get emails into your inbox that 'come from' your domain without it being marked as spam or not reaching your inbox at all.
Once you set up SPF you are a little more secure but you cen actually do even more by using DKIM.
What are DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting and Conformance)?
DKIM and DMARC enable the sender to take responsibility for the emails he/she sends. This is done by ensuring that the email you send contains an encrypted digital signature that only you know about. When someone receives your email with this digital signature it looks at your domain setup (DNS) and from there can retrieve a key to decrypt the digital signature. If it could not be decrypted the email will not reach your inbox and the scam number will be thwarted.







